How To View All Users Registered With My Domain Controller
This browser is no longer supported.
Upgrade to Microsoft Edge to accept reward of the latest features, security updates, and technical support.
Active Directory Accounts
Applies to
- Windows Server 2016
Windows Server operating systems are installed with default local accounts. In addition, yous can create user accounts to meet the requirements of your organization. This reference topic for the IT professional describes the Windows Server default local accounts that are stored locally on the domain controller and are used in Active Directory.
This reference topic does not describe default local user accounts for a member or standalone server or for a Windows customer. For more data, come across Local Accounts.
Most this topic
This topic describes the following:
-
Default local accounts in Agile Directory
-
Administrator account
-
Guest account
-
HelpAssistant account (installed with a Remote Aid session)
-
KRBTGT account
-
-
Settings for default local accounts in Active Directory
-
Manage default local accounts in Active Directory
-
Restrict and protect sensitive domain accounts
-
Separate administrator accounts from user accounts
-
Create dedicated workstation hosts without Cyberspace and email access
-
Restrict administrator logon admission to servers and workstations
-
Disable the account delegation right for administrator accounts
-
-
Secure and manage domain controllers
Default local accounts in Active Directory
Default local accounts are built-in accounts that are created automatically when a Windows Server domain controller is installed and the domain is created. These default local accounts have counterparts in Active Directory. These accounts also have domain-wide access and are completely separate from the default local user accounts for a member or standalone server.
Yous can assign rights and permissions to default local accounts on a particular domain controller, and only on that domain controller. These accounts are local to the domain. Subsequently the default local accounts are installed, they are stored in the Users container in Active Directory Users and Computers. It is a all-time practice to go along the default local accounts in the User container and non try to move these accounts, for example, to a different organizational unit (OU).
The default local accounts in the Users container include: Administrator, Guest, and KRBTGT. The HelpAssistant business relationship is installed when a Remote Assistance session is established. The post-obit sections depict the default local accounts and their use in Agile Directory.
Primarily, default local accounts do the following:
-
Allow the domain represent, place, and cosign the identity of the user that is assigned to the account by using unique credentials (user name and countersign). It is a best practice to assign each user to a unmarried account to ensure maximum security. Multiple users are not immune to share 1 business relationship. A user business relationship lets a user sign in to computers, networks, and domains with a unique identifier that can be authenticated by the estimator, network, or domain.
-
Qualify (grant or deny) access to resources. Afterward a user's credentials have been authenticated, the user is authorized to access the network and domain resources based on the user's explicitly assigned rights on the resource.
-
Audit the actions that are carried out on a user account.
In Agile Directory, default local accounts are used by administrators to manage domain and fellow member servers direct and from defended administrative workstations. Active Directory accounts provide admission to network resources. Active Directory User accounts and Calculator accounts can represent a physical entity, such as a computer or person, or act as dedicated service accounts for some applications.
Each default local account is automatically assigned to a security group that is preconfigured with the appropriate rights and permissions to perform specific tasks. Active Directory security groups collect user accounts, computer accounts, and other groups into manageable units. For more information, see Active Directory Security Groups.
On an Active Directory domain controller, each default local account is referred to equally a security primary. A security main is a directory object that is used to secure and manage Active Directory services that provide access to domain controller resources. A security primary includes objects such as user accounts, reckoner accounts, security groups, or the threads or processes that run in the security context of a user or computer account. For more than information, see Security Principals.
A security principal is represented by a unique security identifier (SID).The SIDs that are related to each of the default local accounts in Active Directory are described in the sections below.
Some of the default local accounts are protected past a groundwork procedure that periodically checks and applies a specific security descriptor. A security descriptor is a data structure that contains security information that is associated with a protected object. This procedure ensures that whatsoever successful unauthorized effort to modify the security descriptor on one of the default local accounts or groups is overwritten with the protected settings.
This security descriptor is present on the AdminSDHolder object. If you want to modify the permissions on 1 of the service administrator groups or on any of its member accounts, you must modify the security descriptor on the AdminSDHolder object to ensure that it is applied consistently. Be careful when making these modifications, considering you are likewise changing the default settings that are applied to all of your protected accounts.
Administrator account
The Ambassador account is a default account that is used in all versions of the Windows operating system on every computer and device. The Ambassador business relationship is used past the system ambassador for tasks that crave administrative credentials. This account cannot exist deleted or locked out, simply the account can exist renamed or disabled.
The Ambassador account gives the user complete access (Full Command permissions) of the files, directories, services, and other resource that are on that local server. The Administrator account can be used to create local users, and assign user rights and access control permissions. Administrator tin also be used to have control of local resource at whatsoever time simply by irresolute the user rights and permissions. Although files and directories tin can be protected from the Administrator account temporarily, the Ambassador account tin take control of these resources at any time by changing the admission permissions.
Account group membership
The Administrator account has membership in the default security groups as described in the Administrator business relationship attributes table afterwards in this topic.
The security groups ensure that y'all can control administrator rights without having to change each Administrator account. In most instances, y'all do not take to change the bones settings for this account. Notwithstanding, you might have to change its advanced settings, such equally membership in particular groups.
Security considerations
Afterward installation of the server operating system, your first chore is to set up up the Ambassador account properties securely. This includes setting upwards an especially long, strong countersign, and securing the Remote command and Remote Desktop Services profile settings.
The Administrator account can as well be disabled when it is not required. Renaming or disabling the Administrator business relationship makes it more difficult for malicious users to endeavour to proceeds access to the account. However, even when the Administrator account is disabled, it can yet be used to gain access to a domain controller by using safe fashion.
On a domain controller, the Administrator account becomes the Domain Admin account. The Domain Admin business relationship is used to sign in to the domain controller and this account requires a strong password. The Domain Admin account gives you access to domain resources.
Annotation
When the domain controller is initially installed, you can sign in and use Server Managing director to fix upward a local Administrator account, with the rights and permissions y'all desire to assign. For example, you can utilise a local Administrator account to manage the operating system when yous kickoff install information technology. By using this approach, you can gear up upward the operating system without getting locked out. Generally, you do not need to utilize the business relationship afterwards installation. You tin can just create local user accounts on the domain controller, before Active Directory Domain Services is installed, and not afterwards.
When Active Directory is installed on the get-go domain controller in the domain, the Administrator account is created for Active Directory. The Administrator account is the well-nigh powerful account in the domain. It is given domain-wide access and administrative rights to administer the calculator and the domain, and it has the almost extensive rights and permissions over the domain. The person who installs Agile Directory Domain Services on the computer creates the password for this business relationship during the installation.
Administrator business relationship attributes
| Attribute | Value |
|---|---|
| Well-Known SID/RID | South-1-5-<domain>-500 |
| Type | User |
| Default container | CN=Users, DC=<domain>, DC= |
| Default members | N/A |
| Default member of | Administrators, Domain Admins, Enterprise Administrators, Domain Users. Note that the Primary Grouping ID of all user accounts is Domain Users. Grouping Policy Creator Owners, and Schema Admins in Agile Directory Domain Users group |
| Protected by ADMINSDHOLDER? | Yes |
| Prophylactic to motion out of default container? | Aye |
| Safe to delegate direction of this group to not-service administrators? | No |
Invitee account
The Guest account is a default local account that has limited access to the computer and is disabled by default. By default, the Guest account countersign is left blank. A blank password allows the Guest business relationship to be accessed without requiring the user to enter a password.
The Invitee account enables occasional or one-time users, who do not have an private business relationship on the computer, to sign in to the local server or domain with restricted rights and permissions. The Invitee account can be enabled, and the password tin can be set if needed, merely only by a member of the Administrator group on the domain.
Account group membership
The Invitee account has membership in the default security groups that are described in the following Guest account attributes tabular array. Past default, the Guest account is the only fellow member of the default Guests grouping, which lets a user sign in to a server, and the Domain Guests global group, which lets a user sign in to a domain.
A member of the Administrators group or Domain Admins grouping tin can set up a user with a Guest account on one or more computers.
Security considerations
Because the Guest business relationship tin provide anonymous access, it is a security gamble. It as well has a well-known SID. For this reason, it is a best practice to leave the Guest account disabled, unless its utilize is required and then but with restricted rights and permissions for a very limited period of time.
When the Guest business relationship is required, an Administrator on the domain controller is required to enable the Guest business relationship. The Guest account tin exist enabled without requiring a password, or it can be enabled with a strong password. The Administrator as well grants restricted rights and permissions for the Guest business relationship. To assistance prevent unauthorized admission:
-
Practice not grant the Guest business relationship the Shut down the arrangement user correct. When a computer is shutting downwardly or starting up, information technology is possible that a Guest user or anyone with local admission, such as a malicious user, could gain unauthorized admission to the computer.
-
Do non provide the Guest account with the ability to view the event logs. After the Guest business relationship is enabled, it is a best practise to monitor this account frequently to ensure that other users cannot utilise services and other resource, such as resources that were unintentionally left available past a previous user.
-
Practice not use the Guest account when the server has external network admission or admission to other computers.
If you decide to enable the Invitee business relationship, be sure to restrict its use and to change the password regularly. As with the Administrator account, you might want to rename the business relationship as an added security precaution.
In add-on, an administrator is responsible for managing the Invitee account. The administrator monitors the Invitee business relationship, disables the Guest account when it is no longer in utilise, and changes or removes the countersign as needed.
For details about the Guest business relationship attributes, see the following table.
Guest account attributes
| Attribute | Value |
|---|---|
| Well-Known SID/RID | Due south-1-five-<domain>-501 |
| Type | User |
| Default container | CN=Users, DC=<domain>, DC= |
| Default members | None |
| Default member of | Guests, Domain Guests |
| Protected by ADMINSDHOLDER? | No |
| Safe to motion out of default container? | Can exist moved out, just we exercise not recommend information technology. |
| Safe to delegate management of this group to non-Service admins? | No |
HelpAssistant business relationship (installed with a Remote Assistance session)
The HelpAssistant business relationship is a default local business relationship that is enabled when a Remote Help session is run. This business relationship is automatically disabled when no Remote Assistance requests are awaiting.
HelpAssistant is the primary business relationship that is used to constitute a Remote Aid session. The Remote Help session is used to connect to some other computer running the Windows operating organization, and information technology is initiated by invitation. For solicited remote aid, a user sends an invitation from their figurer, through e-mail service or as a file, to a person who tin provide assistance. Subsequently the user'southward invitation for a Remote Help session is accepted, the default HelpAssistant account is automatically created to give the person who provides assistance limited access to the computer. The HelpAssistant account is managed by the Remote Desktop Help Session Director service.
Security considerations
The SIDs that pertain to the default HelpAssistant business relationship include:
-
SID: S-one-five-
<domain>-13, brandish name Last Server User. This grouping includes all users who sign in to a server with Remote Desktop Services enabled. Note that, in Windows Server 2008, Remote Desktop Services are chosen Terminal Services. -
SID: South-i-5-
<domain>-xiv, brandish proper name Remote Interactive Logon. This grouping includes all users who connect to the reckoner past using a remote desktop connection. This group is a subset of the Interactive group. Access tokens that contain the Remote Interactive Logon SID besides contain the Interactive SID.
For the Windows Server operating system, Remote Aid is an optional component that is not installed past default. You must install Remote Help before it can be used.
For details about the HelpAssistant business relationship attributes, meet the post-obit tabular array.
HelpAssistant business relationship attributes
| Attribute | Value |
|---|---|
| Well-Known SID/RID | Southward-1-v-<domain>-xiii (Final Server User), S-one-5-<domain>-14 (Remote Interactive Logon) |
| Blazon | User |
| Default container | CN=Users, DC=<domain>, DC= |
| Default members | None |
| Default member of | Domain Guests Guests |
| Protected by ADMINSDHOLDER? | No |
| Condom to move out of default container? | Can be moved out, but we practice not recommend it. |
| Safe to delegate management of this group to non-Service admins? | No |
KRBTGT account
The KRBTGT account is a local default business relationship that acts as a service account for the Key Distribution Center (KDC) service. This account cannot be deleted, and the account name cannot be changed. The KRBTGT account cannot be enabled in Active Directory.
KRBTGT is as well the security principal name used by the KDC for a Windows Server domain, as specified by RFC 4120. The KRBTGT business relationship is the entity for the KRBTGT security principal, and it is created automatically when a new domain is created.
Windows Server Kerberos hallmark is achieved by the use of a special Kerberos ticket-granting ticket (TGT) enciphered with a symmetric key. This key is derived from the password of the server or service to which access is requested. The TGT password of the KRBTGT account is known only by the Kerberos service. In order to request a session ticket, the TGT must be presented to the KDC. The TGT is issued to the Kerberos customer from the KDC.
KRBTGT account maintenance considerations
A stiff password is assigned to the KRBTGT and trust accounts automatically. Like whatsoever privileged service accounts, organizations should change these passwords on a regular schedule. The password for the KDC account is used to derive a secret key for encrypting and decrypting the TGT requests that are issued. The password for a domain trust account is used to derive an inter-realm key for encrypting referral tickets.
Resetting the countersign requires you either to be a member of the Domain Admins group, or to have been delegated with the appropriate authority. In addition, y'all must be a member of the local Administrators grouping, or you must accept been delegated the appropriate authorization.
Later you reset the KRBTGT password, ensure that event ID 9 in the (Kerberos) Key-Distribution-Centre event source is written to the System issue log.
Security considerations
It is besides a best practice to reset the KRBTGT account password to ensure that a newly restored domain controller does not replicate with a compromised domain controller. In this case, in a large woods recovery that is spread across multiple locations, you cannot guarantee that all domain controllers are close downwardly, and if they are shut down, they cannot be rebooted once again before all of the advisable recovery steps have been undertaken. After yous reset the KRBTGT account, another domain controller cannot replicate this account password by using an old password.
An organisation suspecting domain compromise of the KRBTGT account should consider the employ of professional incident response services. The impact to restore the buying of the account is domain-broad and labor intensive an should exist undertaken equally part of a larger recovery effort.
The KRBTGT password is the central from which all trust in Kerberos chains up to. Resetting the KRBTGT password is similar to renewing the root CA certificate with a new primal and immediately not trusting the old central, resulting in almost all subsequent Kerberos operations will be affected.
For all business relationship types (users, computers, and services)
-
All the TGTs that are already issued and distributed volition be invalid because the DCs will reject them. These tickets are encrypted with the KRBTGT so any DC tin can validate them. When the countersign changes, the tickets go invalid.
-
All currently authenticated sessions that logged on users have established (based on their service tickets) to a resource (such as a file share, SharePoint site, or Exchange server) are good until the service ticket is required to re-authenticate.
-
NTLM authenticated connections are not affected
Considering it is incommunicable to predict the specific errors that volition occur for whatsoever given user in a production operating surroundings, you must presume all computers and users volition exist affected.
Important
Rebooting a figurer is the but reliable mode to recover functionality as this will cause both the computer business relationship and user accounts to log back in again. Logging in once more will request new TGTs that are valid with the new KRBTGT, correcting any KRBTGT related operational issues on that reckoner.
For information nigh how to assistance mitigate the risks associated with a potentially compromised KRBTGT account, meet KRBTGT Account Password Reset Scripts now available for customers.
Read-merely domain controllers and the KRBTGT account
Windows Server 2008 introduced the read-only domain controller (RODC). The RODC is advertised equally the Key Distribution Middle (KDC) for the branch office. The RODC uses a different KRBTGT account and password than the KDC on a writable domain controller when it signs or encrypts ticket-granting ticket (TGT) requests. Afterward an account is successfully authenticated, the RODC determines if a user'due south credentials or a computer's credentials can be replicated from the writable domain controller to the RODC by using the Password Replication Policy.
Subsequently the credentials are cached on the RODC, the RODC can accept that user's sign-in requests until the credentials modify. When a TGT is signed with the KRBTGT account of the RODC, the RODC recognizes that information technology has a cached copy of the credentials. If another domain controller signs the TGT, the RODC forwards requests to a writable domain controller.
KRBTGT business relationship attributes
For details about the KRBTGT account attributes, run across the following table.
| Attribute | Value |
|---|---|
| Well-Known SID/RID | S-ane-5-<domain>-502 |
| Type | User |
| Default container | CN=Users, DC=<domain>, DC= |
| Default members | None |
| Default member of | Domain Users group. Note that the Chief Group ID of all user accounts is Domain Users. |
| Protected past ADMINSDHOLDER? | Yeah |
| Safe to move out of default container? | Can be moved out, but we do not recommend it. |
| Safety to delegate direction of this group to non-Service admins? | No |
Settings for default local accounts in Active Directory
Each default local business relationship in Active Directory has a number of account settings that you can utilize to configure countersign settings and security-specific information, as described in the following tabular array.
Settings for default local accounts in Agile Directory
| Account settings | Description |
|---|---|
| User must change password at adjacent logon | Forces a password change the side by side time that the user logs signs in to the network. Utilise this option when you desire to ensure that the user is the only person to know his or her password. |
| User cannot alter password | Prevents the user from changing the password. Use this option when yous want to maintain command over a user account, such equally for a Guest or temporary account. |
| Countersign never expires | Prevents a user password from expiring. Information technology is a best practice to enable this selection with service accounts and to apply stiff passwords. |
| Store passwords using reversible encryption | Provides support for applications that use protocols requiring noesis of the plaintext form of the user's password for authentication purposes. This option is required when using Challenge Handshake Authentication Protocol (CHAP) in Net Authentication Services (IAS), and when using digest authentication in Cyberspace Information Services (IIS). |
| Business relationship is disabled | Prevents the user from signing in with the selected account. Equally an administrator, you can use disabled accounts every bit templates for mutual user accounts. |
| Smart card is required for interactive logon | Requires that a user has a smart card to sign on to the network interactively. The user must besides have a smart card reader attached to their reckoner and a valid personal identification number (Pin) for the smart card. When this attribute is applied on the account, the consequence is as follows: |
| Account is trusted for delegation | Lets a service running nether this business relationship perform operations on behalf of other user accounts on the network. A service running under a user business relationship (besides known every bit a service business relationship) that is trusted for delegation can impersonate a client to gain admission to resource, either on the reckoner where the service is running or on other computers. For example, in a woods that is set to the Windows Server 2003 functional level, this setting is plant on the Delegation tab. It is bachelor just for accounts that have been assigned service principal names (SPNs), which are set by using the setspn control from Windows Support Tools. This setting is security-sensitive and should be assigned charily. |
| Account is sensitive and cannot be delegated | Gives control over a user account, such every bit for a Guest account or a temporary account. This option can exist used if this business relationship cannot be assigned for delegation by another business relationship. |
| Use DES encryption types for this account | Provides support for the Information Encryption Standard (DES). DES supports multiple levels of encryption, including Microsoft Signal-to-Point Encryption (MPPE) Standard (40-flake and 56-scrap), MPPE standard (56-chip), MPPE Strong (128-flake), Net Protocol security (IPSec) DES (40-scrap), IPSec 56-bit DES, and IPSec Triple DES (3DES). Note: DES is not enabled past default in Windows Server operating systems starting with Windows Server 2008 R2, nor in Windows client operating systems starting with Windows 7. For these operating systems, computers volition non utilise DES-CBC-MD5 or DES-CBC-CRC cipher suites past default. If your environment requires DES, so this setting might affect compatibility with client computers or services and applications in your environment. For more information, see Hunting down DES in order to securely deploy Kerberos |
| Do not require Kerberos preauthentication | Provides support for alternate implementations of the Kerberos protocol. Because preauthentication provides boosted security, employ caution when enabling this pick. Note that domain controllers running Windows 2000 or Windows Server 2003 tin apply other mechanisms to synchronize time. |
Manage default local accounts in Active Directory
Subsequently the default local accounts are installed, these accounts reside in the Users container in Agile Directory Users and Computers. Default local accounts can be created, disabled, reset, and deleted past using the Active Directory Users and Computers Microsoft Management Panel (MMC) and by using command-line tools.
Y'all can use Active Directory Users and Computers to assign rights and permissions on a given local domain controller, and that domain controller merely, to limit the ability of local users and groups to perform sure actions. A right authorizes a user to perform certain actions on a estimator, such equally bankroll upward files and folders or shutting downwards a computer. In contrast, an access permission is a rule that is associated with an object, unremarkably a file, folder, or printer, that regulates which users can have access to the object and in what manner.
For more information virtually creating and managing local user accounts in Active Directory, see Manage Local Users.
You tin can likewise use Active Directory Users and Computers on a domain controller to target remote computers that are non domain controllers on the network.
Y'all tin obtain recommendations from Microsoft for domain controller configurations that y'all can distribute by using the Security Compliance Managing director (SCM) tool. For more information, run into Microsoft Security Compliance Manager.
Some of the default local user accounts are protected by a background process that periodically checks and applies a specific security descriptor, which is a data structure that contains security data that is associated with a protected object. This security descriptor is present on the AdminSDHolder object.
This means, when you want to modify the permissions on a service administrator grouping or on any of its member accounts, you are also required to modify the security descriptor on the AdminSDHolder object. This approach ensures that the permissions are applied consistently. Be careful when you make these modifications, because this activeness tin can besides bear on the default settings that are applied to all of your protected authoritative accounts.
Restrict and protect sensitive domain accounts
Restricting and protecting domain accounts in your domain environment requires you to adopt and implement the following all-time practices approach:
-
Strictly limit membership to the Administrators, Domain Admins, and Enterprise Admins groups.
-
Stringently command where and how domain accounts are used.
Member accounts in the Administrators, Domain Admins, and Enterprise Admins groups in a domain or wood are high-value targets for malicious users. Information technology is a best do to strictly limit membership to these ambassador groups to the smallest number of accounts in club to limit any exposure. Restricting membership in these groups reduces the possibility that an administrator might unintentionally misuse these credentials and create a vulnerability that malicious users tin can exploit.
Moreover, information technology is a best practise to stringently control where and how sensitive domain accounts are used. Restrict the use of Domain Admins accounts and other administrator accounts to preclude them from being used to sign in to direction systems and workstations that are secured at the same level equally the managed systems. When administrator accounts are not restricted in this manner, each workstation from which a domain administrator signs in provides some other location that malicious users can exploit.
Implementing these all-time practices is separated into the following tasks:
-
Separate administrator accounts from user accounts
-
Create dedicated workstation hosts for administrators
-
Restrict administrator logon access to servers and workstations
-
Disable the account delegation right for ambassador accounts
Annotation that, to provide for instances where integration challenges with the domain environs are expected, each task is described co-ordinate to the requirements for a minimum, better, and ideal implementation. As with all significant changes to a production environment, ensure that you lot examination these changes thoroughly earlier you implement and deploy them. And so stage the deployment in a manner that allows for a rollback of the alter in case technical issues occur.
Divide administrator accounts from user accounts
Restrict Domain Admins accounts and other sensitive accounts to prevent them from being used to sign in to lower trust servers and workstations. Restrict and protect administrator accounts by segregating administrator accounts from standard user accounts, past separating authoritative duties from other tasks, and by limiting the employ of these accounts. Create defended accounts for administrative personnel who require administrator credentials to perform specific administrative tasks, and then create separate accounts for other standard user tasks, according to the following guidelines:
-
Privileged account. Allocate ambassador accounts to perform the post-obit authoritative duties only:
-
Minimum. Create separate accounts for domain administrators, enterprise administrators, or the equivalent with appropriate administrator rights in the domain or forest. Utilize accounts that accept been granted sensitive administrator rights only to administer domain data and domain controllers.
-
Improve. Create separate accounts for administrators that have reduced administrative rights, such as accounts for workstation administrators, and accounts with user rights over designated Agile Directory organizational units (OUs).
-
Ideal. Create multiple, separate accounts for an ambassador who has a multifariousness of job responsibilities that require different trust levels. Set up each ambassador account with significantly different user rights, such every bit for workstation administration, server administration and domain administration, to allow the administrator sign in to given workstations, servers and domain controllers based strictly on his or her chore responsibilities.
-
-
Standard user account. Grant standard user rights for standard user tasks, such as email, web browsing, and using line-of-business organisation (LOB) applications. These accounts should not exist granted ambassador rights.
Important
Ensure that sensitive ambassador accounts cannot admission email or browse the Internet as described in the following department.
Create dedicated workstation hosts without Internet and email access
Administrators need to manage job responsibilities that require sensitive ambassador rights from a dedicated workstation because they do not have easy physical access to the servers. A workstation that is connected to the Internet and has email and web browsing access is regularly exposed to compromise through phishing, downloading, and other types of Internet attacks. Because of these threats, information technology is a best practice to set these administrators up past using workstations that are dedicated to administrative duties just, and not provide admission to the Internet, including email and web browsing. For more information, see Carve up administrator accounts from user accounts.
Notation
If the administrators in your environment tin sign in locally to managed servers and perform all tasks without elevated rights or domain rights from their workstation, you can skip this job.
-
Minimum. Build defended authoritative workstations and cake Internet access on those workstations including web browsing and email. Use the following ways to cake Internet admission:
-
Configure authenticating boundary proxy services, if they are deployed, to disallow administrator accounts from accessing the Internet.
-
Configure boundary firewall or proxy services to disallow Internet access for the IP addresses that are assigned to dedicated authoritative workstations.
-
Block outbound access to the boundary proxy servers in the Windows Firewall.
The instructions for meeting this minimum requirement are described in the following procedure.
-
-
Meliorate. Do not grant administrators membership in the local Administrator group on the computer in order to restrict the administrator from bypassing these protections.
-
Ideal. Restrict workstations from having whatever network connectivity, except for the domain controllers and servers that the administrator accounts are used to manage. Alternately, use AppLocker application control policies to restrict all applications from running, except for the operating system and canonical administrative tools and applications. For more data well-nigh AppLocker, run across AppLocker.
The post-obit procedure describes how to block Internet access by creating a Group Policy Object (GPO) that configures an invalid proxy accost on authoritative workstations. These instructions apply merely to computers running Net Explorer and other Windows components that use these proxy settings.
Note
In this procedure, the workstations are defended to domain administrators. By merely modifying the administrator accounts to grant permission to administrators to sign in locally, you can create additional OUs to manage administrators that take fewer authoritative rights to use the instructions described in the following procedure.
To install administrative workstations in a domain and cake Net and e-mail access (minimum)
-
As a domain administrator on a domain controller, open Active Directory Users and Computers, and create a new OU for authoritative workstations.
-
Create computer accounts for the new workstations.

-
Close Active Directory Users and Computers.
-
Start the Group Policy Management Panel (GPMC).
-
Right-click the new OU, and > Create a GPO in this domain, and Link information technology hither.
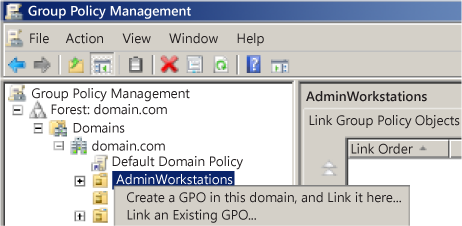
-
Name the GPO, and > OK.
-
Expand the GPO, correct-click the new GPO, and > Edit.

-
Configure which members of accounts tin can log on locally to these administrative workstations every bit follows:
-
Navigate to Computer Configuration\Policies\Windows Settings\Local Policies, and so click User Rights Assignment.
-
Double-click Allow log on locally, and and then select the Define these policy settings bank check box.
-
Click Add User or Group > Browse, type Enterprise Admins, and > OK.
-
Click Add User or Group > Browse, type Domain Admins, and > OK.
Important
These instructions presume that the workstation is to be dedicated to domain administrators.
-
Click Add User or Group, blazon Administrators, and > OK.

-
-
Configure the proxy configuration:
-
Navigate to User Configuration\Policies\Windows Settings\Net Explorer, and > Connectedness.
-
Double-click Proxy Settings, select the Enable proxy settings check box, type 127.0.0.1 (the network Loopback IP address) as the proxy accost, and > OK.
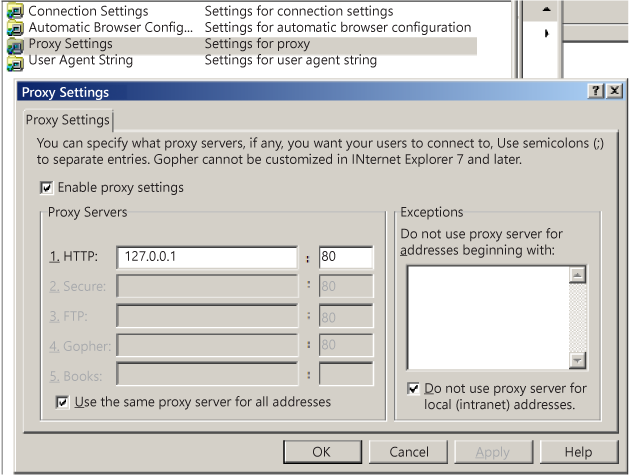
-
-
Configure the loopback processing mode to enable the user Group Policy proxy setting to employ to all users on the figurer equally follows:
-
Navigate to Figurer Configuration\Policies\Administrative Templates\System, and > Group Policy.
-
Double-click User Group Policy loopback policy processing mode, and > Enabled.
-
Select Merge Mode, and > OK.
-
-
Configure software updates equally follows:
-
Navigate to Computer Configuration\Policies\Administrative Templates\Windows Components, and then click Windows Update.
-
Configure Windows Update settings as described in the following table.
Windows Update Setting Configuration Allow Automated Updates immediate installation Enabled Configure Automatic Updates Enabled4 - Auto download and schedule the installation0 - Every day 03:00 Enable Windows Update Power Management to automatically wake upwardly the system to install scheduled updates Enabled Specify intranet Microsoft Update service location Enabled http://<WSUSServername> http://<WSUSServername>Where<WSUSServername>is the DNS name or IP address of the Windows Server Update Services (WSUS) in the environment.Automatic Updates detection frequency 6 hours Re-prompt for restart with scheduled installations ane infinitesimal Delay restart for scheduled installations 5 minutes Annotation
This step assumes that Windows Server Update Services (WSUS) is installed and configured in the environment. You tin can skip this step if you use another tool to deploy software updates. Besides, if the public Microsoft Windows Update service only is used on the Net, then these administrative workstations no longer receive updates.
-
-
Configure the inbound firewall to block all connections as follows:
-
Correct-click Windows Firewall with Advanced Security LDAP://path, and > Properties.

-
On each contour, ensure that the firewall is enabled and that inbound connections are set to Block all connections.

-
Click OK to consummate the configuration.
-
-
Close the Group Policy Management Panel.
-
Install the Windows operating system on the workstations, requite each workstation the same names every bit the computer accounts assigned to them, and so join them to the domain.
Restrict administrator logon access to servers and workstations
It is a best practice to restrict administrators from using sensitive administrator accounts to sign in to lower-trust servers and workstations. This restriction prevents administrators from inadvertently increasing the risk of credential theft by signing in to a lower-trust computer.
Important
Ensure that yous either accept local access to the domain controller or that you take built at to the lowest degree one dedicated administrative workstation.
Restrict logon access to lower-trust servers and workstations by using the following guidelines:
-
Minimum. Restrict domain administrators from having logon access to servers and workstations. Earlier starting this procedure, identify all OUs in the domain that contain workstations and servers. Any computers in OUs that are not identified will non restrict administrators with sensitive accounts from signing-in to them.
-
Better. Restrict domain administrators from non-domain controller servers and workstations.
-
Ideal. Restrict server administrators from signing in to workstations, in addition to domain administrators.
Note
For this procedure, do non link accounts to the OU that contain workstations for administrators that perform assistants duties simply, and do not provide Internet or electronic mail admission. For more than information, see Create dedicated workstation hosts for administrators
To restrict domain administrators from workstations (minimum)
-
As a domain administrator, open the Group Policy Management Panel (GPMC).
-
Open Group Policy Management, and expand <forest>\Domains\
<domain>, and then expand to Group Policy Objects. -
Right-click Grouping Policy Objects, and > New.
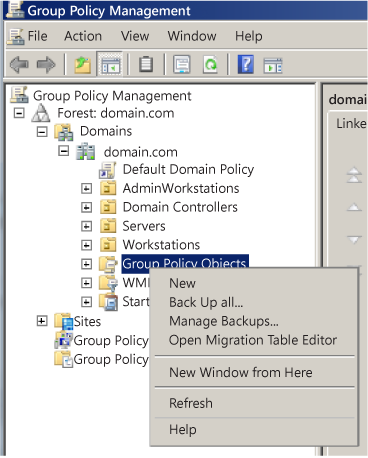
-
In the New GPO dialog box, name the GPO that restricts administrators from signing in to workstations, and > OK.

-
Right-click New GPO, and > Edit.
-
Configure user rights to deny logon locally for domain administrators.
-
Navigate to Figurer Configuration\Policies\Windows Settings\Local Policies, and so click User Rights Assignment, and perform the post-obit:
-
Double-click Deny logon locally, and > Define these policy settings.
-
Click Add User or Group, click Browse, blazon Enterprise Admins, and > OK.
-
Click Add User or Group, click Scan, type Domain Admins, and > OK.

Note
You tin optionally add together any groups that contain server administrators who you want to restrict from signing in to workstations.
-
Click OK to consummate the configuration.
-
-
Configure the user rights to deny batch and service logon rights for domain administrators every bit follows:
Annotation
Completing this step might cause bug with ambassador tasks that run as scheduled tasks or services with accounts in the Domain Admins group. The exercise of using domain ambassador accounts to run services and tasks on workstations creates a significant risk of credential theft attacks and therefore should be replaced with alternative means to run scheduled tasks or services.
-
Double-click Deny logon as a batch job, and > Define these policy settings.
-
Click Add User or Group > Scan, type Enterprise Admins, and > OK.
-
Click Add User or Group > Browse, type Domain Admins, and > OK.

Note
You can optionally add together whatever groups that contain server administrators who you want to restrict from signing in to workstations.
-
Double-click Deny logon equally a service, and > Define these policy settings.
-
Click Add User or Grouping > Browse, type Enterprise Admins, and > OK.
-
Click Add User or Group > Browse, type Domain Admins, and > OK.

Note
You can optionally add together whatever groups that contain server administrators who yous want to restrict from signing in to workstations.
-
-
Link the GPO to the first Workstations OU.
Navigate to the <wood>\Domains\
<domain>\OU Path, and and so:-
Right-click the workstation OU, and and so > Link an Existing GPO.

-
Select the GPO that you but created, and > OK.
 =======
======= 
-
Select the GPO that you just created, and > OK.

-
-
Test the functionality of enterprise applications on workstations in the outset OU and resolve whatsoever bug caused past the new policy.
-
Link all other OUs that comprise workstations.
However, practise not create a link to the Authoritative Workstation OU if it is created for administrative workstations that are dedicated to assistants duties only, and that are without Cyberspace or electronic mail access. For more than information, see Create dedicated workstation hosts for administrators.
Important
If you lot later on extend this solution, practice non deny logon rights for the Domain Users grouping. The Domain Users group includes all user accounts in the domain, including Users, Domain Administrators, and Enterprise Administrators.
Disable the account delegation right for sensitive ambassador accounts
Although user accounts are non marked for delegation by default, accounts in an Active Directory domain tin be trusted for delegation. This means that a service or a figurer that is trusted for delegation tin impersonate an account that authenticates to them to admission other resources across the network.
For sensitive accounts, such as those belonging to members of the Administrators, Domain Admins, or Enterprise Admins groups in Active Directory, delegation can present a substantial take chances of rights escalation. For example, if an account in the Domain Admins group is used to sign in to a compromised member server that is trusted for delegation, that server can asking admission to resource in the context of the Domain Admins business relationship, and escalate the compromise of that member server to a domain compromise.
It is a best practise to configure the user objects for all sensitive accounts in Active Directory by selecting the Account is sensitive and cannot be delegated check box under Account options to prevent these accounts from being delegated. For more information, encounter Setting for default local accounts in Active Directory.
As with whatever configuration change, test this enabled setting fully to ensure that it performs correctly before you implement it.
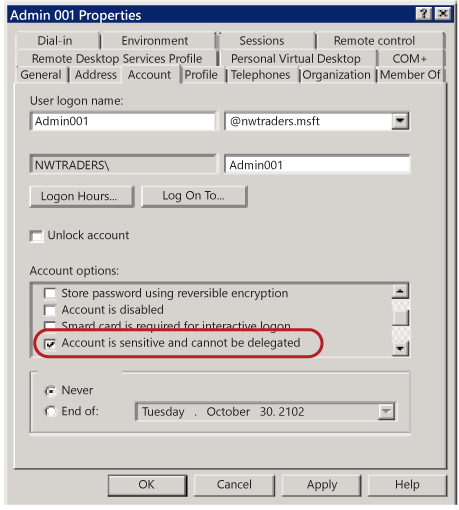
Secure and manage domain controllers
It is a best do to strictly enforce restrictions on the domain controllers in your surround. This ensures that the domain controllers:
-
Run only required software
-
Required software is regularly updated
-
Are configured with the advisable security settings
1 aspect of securing and managing domain controllers is to ensure that the default local user accounts are fully protected. It is of primary importance to restrict and secure all sensitive domain accounts, equally described in the preceding sections.
Because domain controllers store credential password hashes of all accounts in the domain, they are loftier-value targets for malicious users. When domain controllers are not well managed and secured by using restrictions that are strictly enforced, they can be compromised past malicious users. For instance, a malicious user could steal sensitive domain administrator credentials from one domain controller, and so use these credentials to attack the domain and forest.
In addition, installed applications and management agents on domain controllers might provide a path for escalating rights that malicious users can employ to compromise the management service or administrators of that service. The direction tools and services, which your organization uses to manage domain controllers and their administrators, are equally important to the security of the domain controllers and the domain administrator accounts. Ensure that these services and administrators are fully secured with equal effort.
See also
-
Security Principals
-
Access Command Overview
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/active-directory-accounts
Posted by: gentryolis1978.blogspot.com


0 Response to "How To View All Users Registered With My Domain Controller"
Post a Comment